Secure IT Networks
Implementing Vulnerability Management
The growing number of endpoints, servers, network components, physical and virtual appliances, mobile and IoT devices, cloud infrastructures, and even industrial and operational systems dramatically increases the attack surface.
Vulnerability Management allows you to automate the detection of risks through scans and audits – giving you a clear, up-to-date view of your security posture. Actionable recommendations for mitigation (e.g., patches or configuration changes) help shape a proactive and innovative security strategy.
Security Orchestration & Management
Network changes are often time-consuming, and manual processes increase the likelihood of human error. Ensuring compliance and maintaining proper documentation can drain internal resources and drive up operational costs.
Efficiently managing increasingly complex IT networks has a direct impact on your overall security posture. Automated security management streamlines workflows, enforces policies, and generates reports – significantly reducing error rates and operational overhead.
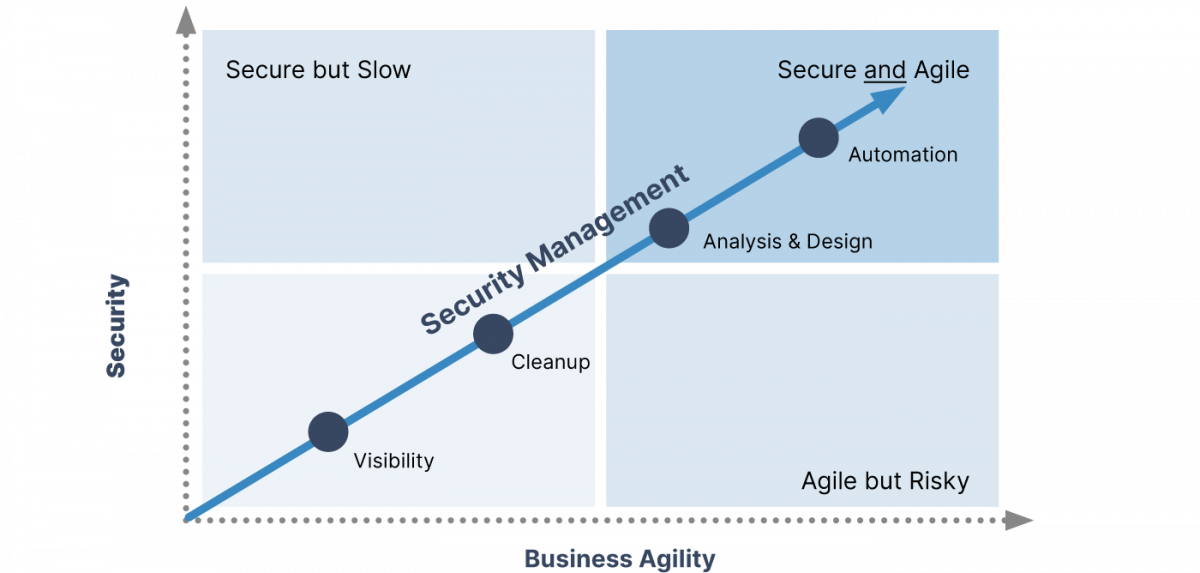
Automated Management
Our experienced security management experts develop tailored solutions and integrate them with your existing technologies. We support you in analyzing your current security landscape and provide guidance for implementing a centralized security strategy step-by-step.
- As s your expert partner, we help increase your organization’s agility through automation, improved Visibility & Compliance, comprehensive security change management, and security policy orchestration.
- With our vulnerability management solutions, you can detect weaknesses, maintain real-time insight into your security status, and prioritize the most impactful improvements – enabling you to take targeted action.
- Automated and standardized workflows, reporting, and collaboration tools allow you to manage your IT networks securely and cost-effectively.
- SIEM and logging solutions standardize the collection and processing of security information, making it easier to enforce policies and integrate them into your infrastructure.
As your trusted partner, we support the implementation, operation, and continuous development of cost-effective security management solutions. With our concepts and expertise, you gain comprehensive protection for your IT networks – and the clarity and control needed to manage your security posture effectively.
Our Security Management Solutions
Expert lecture on the topic:
Our technology partners for security management

Bacher Systems is Forescout’s trusted partner in Austria.


