Proper Encryption Begins with Strong Key Management
Establishing Centralized Key Management
In many IT environments, cryptographic keys are poorly secured: private keys stored on web servers, unprotected root keys in PKI systems, and similar vulnerabilities are widespread.
These practices compromise your control over encryption keys and the data they protect. By implementing a centralized, well-managed crypto infrastructure and a clear cryptographic strategy, you eliminate these risks and establish a high level of data security.
Cloud Usage & Public Key Infrastructure
Encrypting systems in IaaS environments and data in SaaS applications is a fundamental step toward secure cloud adoption. With the right security measures, you retain centralized control – because without access to the keys, stolen data remains unusable.
Storing keys in Hardware Security Modules (HSMs) ensures tamper-proof and theft-resistant protection of sensitive information.
Crypto Management – Efficient & Secure
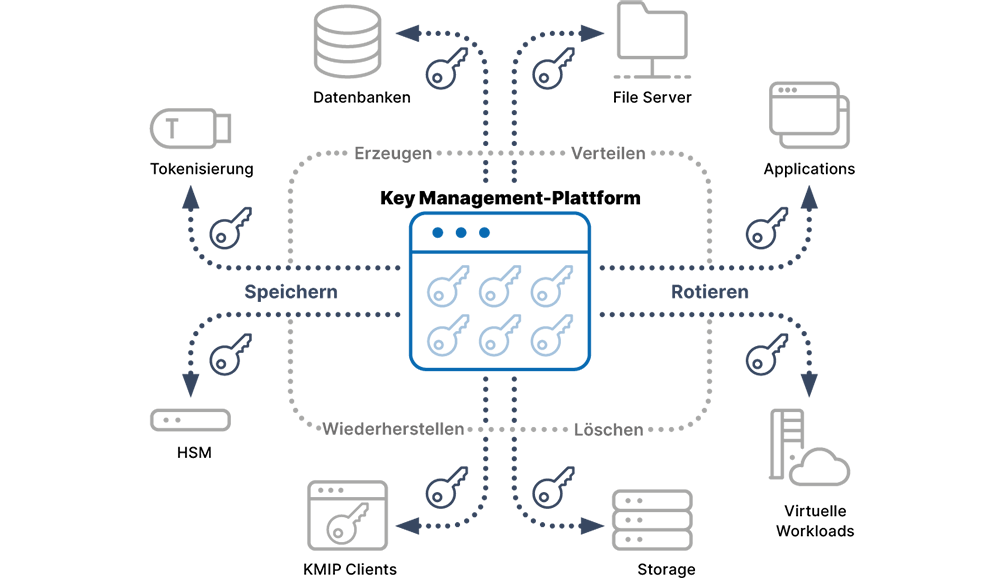
Crypto-Management
- Our experienced IT experts support you, also in cloud environments, to maintain control over your data and manage it securely. With our solutions, you minimize the risk of losing key material.
- As a competent partner, we jointly identify sensitive data and develop a comprehensive concept for your Data Security. A Proof of Value gives you assurance before we integrate Crypto-Management into your IT environment.
- With encryption, you protect your data from misuse and loss. Combined with a central Key Management and the storage of keys in Hardware Security Modules (HSM), you benefit multiple times: from lower operational costs, increased efficiency, and enhanced security.
- Our experts will show you how central Crypto-Management simplifies operations within the company. They will demonstrate how you can always keep track of the keys used.
- We assist you in meeting compliance requirements such as SWIFT, PCI-DSS, etc. through the use of encryption and tokenization.
- As an expert in Data Security & Encryption, we know how to combine performance and encryption. We are happy to integrate your cloud services using the Bring Your Own Key method.
Our Data Security & Encryption Solutions
- Encryption of databases, file servers, applications, workloads, storages, etc.
- secure storage of keys in Hardware Security Modules (HSM)
- central management and secure deletion of keys
- protection against counterfeit keys and certificates
- anonymization of personal data
- secure communication (mail, web services) and compliance
With the right crypto strategy, you ensure greater Data Security. As your thinking partner, we support you in building a central Key Management. Minimize the risks of theft or misuse of your data with us!
Our Data Security & Encryption Solutions
- Encryption for databases, file servers, applications, workloads, storage, and more
- Secure key storage using Hardware Security Modules (HSM)
- Centralized management and secure deletion of cryptographic keys
- Protection against fake keys and certificates
- Anonymization of personal data
- Secure communication (email, web services) and compliance support
Achieve stronger data Security with the right Crypto Strategy
As your IT partner, we help you build a centralized key management system and reduce the risk of data theft or misuse. Together, we strengthen the security of your digital assets.

