Secure Cloud Computing
Define Your Security Responsibilities
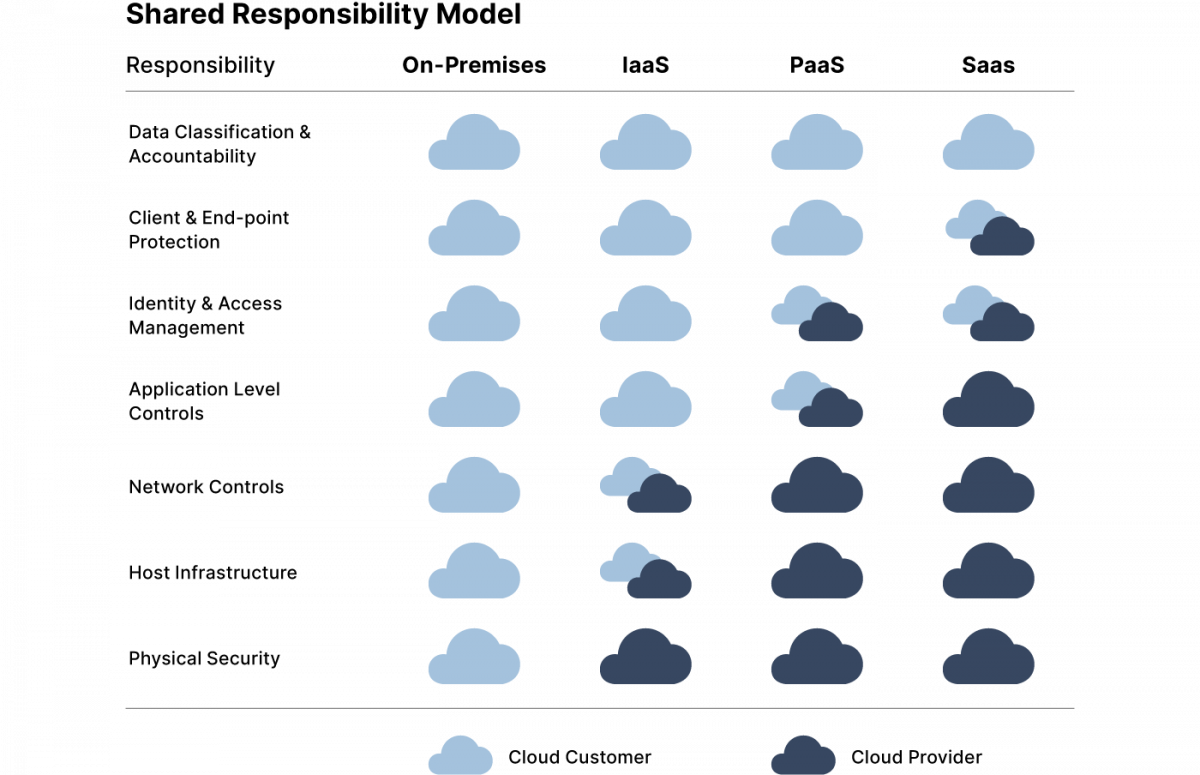
Cloud computing is based on Shared Responsibility Models, which define how responsibilities are divided between cloud service providers and customers. Cloud computing is only secure when you actively fulfill your part of the responsibility.
Depending on your deployment model (private, public, multi, or hybrid cloud) and service model (SaaS, PaaS, IaaS, or a combination), your organization retains greater or lesser responsibility for protecting resources. These may include cloud workloads, network controls, identities, applications, and all data processed within the cloud.
Tailored Cloud Security
As your experienced IT partner, we support you in fulfilling your responsibilities within the shared responsibility framework. We also help address your specific security requirements and implement security controls – even beyond the boundaries of your cloud provider’s environment.
We provide you with cloud security solutions customized to your needs. These solutions help you defend your cloud-based assets and data against cyber attacks and prevent data breaches effectively.
Comprehensive Security Solutions
Our IT experts are familiar with the best-fit security solutions to help your organization securely use cloud services and protect data stored online from threats and misuse.
- We are your reliable partner for expert guidance on cloud security best practices, principles, and architectural strategies. We plan and implement secure, enterprise-wide solutions tailored to your organization.
- We know the native security services provided by cloud vendors and understand how to leverage them effectively. Using this knowledge, we combine the right native features with technologies from our trusted partners to build a security solution tailored to your needs.
- As your competent advisor, we help you maintain a comprehensive overview of your cloud security posture – enabling secure cloud usage across systems and platforms.
With us at your side, you fulfill all security requirements related to cloud technologies and conduct your cloud operations securely – today and in the future.
Expert lecture on the topic:
Our technology partners for Cloud Security

Bacher Systems is Forescout’s trusted partner in Austria.



